- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Phrack Magazine: Digital hacking magazine.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
Tuesday, June 30, 2020
Top 15 Free Websites to Learn Hacking this 2018
Posted by Ki-te at 8:30 PM 0 comments
Thursday, June 11, 2020
DOS (Denial Of Service) Attack Tutorial Ping Of Death ;DDOS
What is DoS Attack?
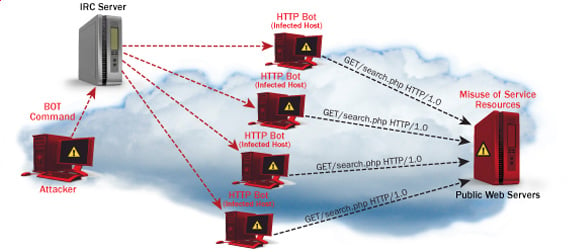
DOS is an attack used to deny legitimate users access to a resource such as accessing a website, network, emails, etc. or making it extremely slow. DoS is the acronym for Denial of Service. This type of attack is usually implemented by hitting the target resource such as a web server with too many requests at the same time. This results in the server failing to respond to all the requests. The effect of this can either be crashing the servers or slowing them down.
Cutting off some business from the internet can lead to significant loss of business or money. The internet and computer networks power a lot of businesses. Some organizations such as payment gateways, e-commerce sites entirely depend on the internet to do business.
In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks.
Topics covered in this tutorial
- Types of Dos Attacks
- How DoS attacks work
- DoS attack tools
- DoS Protection: Prevent an attack
- Hacking Activity: Ping of Death
- Hacking Activity: Launch a DOS attack
Types of Dos Attacks
There are two types of Dos attacks namely;
- DoS– this type of attack is performed by a single host
- Distributed DoS– this type of attack is performed by a number of compromised machines that all target the same victim. It floods the network with data packets.
How DoS attacks work
Let's look at how DoS attacks are performed and the techniques used. We will look at five common types of attacks.
Ping of Death
The ping command is usually used to test the availability of a network resource. It works by sending small data packets to the network resource. The ping of death takes advantage of this and sends data packets above the maximum limit (65,536 bytes) that TCP/IP allows. TCP/IP fragmentation breaks the packets into small chunks that are sent to the server. Since the sent data packages are larger than what the server can handle, the server can freeze, reboot, or crash.
Smurf
This type of attack uses large amounts of Internet Control Message Protocol (ICMP) ping traffic target at an Internet Broadcast Address. The reply IP address is spoofed to that of the intended victim. All the replies are sent to the victim instead of the IP used for the pings. Since a single Internet Broadcast Address can support a maximum of 255 hosts, a smurf attack amplifies a single ping 255 times. The effect of this is slowing down the network to a point where it is impossible to use it.
Buffer overflow
A buffer is a temporal storage location in RAM that is used to hold data so that the CPU can manipulate it before writing it back to the disc. Buffers have a size limit. This type of attack loads the buffer with more data that it can hold. This causes the buffer to overflow and corrupt the data it holds. An example of a buffer overflow is sending emails with file names that have 256 characters.
Teardrop
This type of attack uses larger data packets. TCP/IP breaks them into fragments that are assembled on the receiving host. The attacker manipulates the packets as they are sent so that they overlap each other. This can cause the intended victim to crash as it tries to re-assemble the packets.
SYN attack
SYN is a short form for Synchronize. This type of attack takes advantage of the three-way handshake to establish communication using TCP. SYN attack works by flooding the victim with incomplete SYN messages. This causes the victim machine to allocate memory resources that are never used and deny access to legitimate users.
DoS attack tools
The following are some of the tools that can be used to perform DoS attacks.
- Nemesy– this tool can be used to generate random packets. It works on windows. This tool can be downloaded from http://packetstormsecurity.com/files/25599/nemesy13.zip.html . Due to the nature of the program, if you have an antivirus, it will most likely be detected as a virus.
- Land and LaTierra– this tool can be used for IP spoofing and opening TCP connections
- Blast– this tool can be downloaded from http://www.opencomm.co.uk/products/blast/features.php
- Panther- this tool can be used to flood a victim's network with UDP packets.
- Botnets– these are multitudes of compromised computers on the Internet that can be used to perform a distributed denial of service attack.
DoS Protection: Prevent an attack
An organization can adopt the following policy to protect itself against Denial of Service attacks.
- Attacks such as SYN flooding take advantage of bugs in the operating system. Installing security patches can help reduce the chances of such attacks.
- Intrusion detection systems can also be used to identify and even stop illegal activities
- Firewalls can be used to stop simple DoS attacks by blocking all traffic coming from an attacker by identifying his IP.
- Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic.
Hacking Activity: Ping of Death
We will assume you are using Windows for this exercise. We will also assume that you have at least two computers that are on the same network. DOS attacks are illegal on networks that you are not authorized to do so. This is why you will need to setup your own network for this exercise.
Open the command prompt on the target computer
Enter the command ipconfig. You will get results similar to the ones shown below
For this example, we are using Mobile Broadband connection details. Take note of the IP address. Note: for this example to be more effective, and you must use a LAN network.
Switch to the computer that you want to use for the attack and open the command prompt
We will ping our victim computer with infinite data packets of 65500
Enter the following command
ping 10.128.131.108 –t |65500
HERE,
- "ping" sends the data packets to the victim
- "10.128.131.108" is the IP address of the victim
- "-t" means the data packets should be sent until the program is stopped
- "-l" specifies the data load to be sent to the victim
You will get results similar to the ones shown below
Flooding the target computer with data packets doesn't have much effect on the victim. In order for the attack to be more effective, you should attack the target computer with pings from more than one computer.
The above attack can be used to attacker routers, web servers etc.
If you want to see the effects of the attack on the target computer, you can open the task manager and view the network activities.
- Right click on the taskbar
- Select start task manager
- Click on the network tab
- You will get results similar to the following
If the attack is successful, you should be able to see increased network activities.
Hacking Activity: Launch a DOS attack
In this practical scenario, we are going to use Nemesy to generate data packets and flood the target computer, router or server.
As stated above, Nemesy will be detected as an illegal program by your anti-virus. You will have to disable the anti-virus for this exercise.
- Download Nemesy from http://packetstormsecurity.com/files/25599/nemesy13.zip.html
- Unzip it and run the program Nemesy.exe
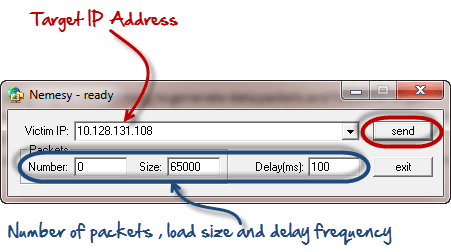
- You will get the following interface
Enter the target IP address, in this example; we have used the target IP we used in the above example.
HERE,
- 0 as the number of packets means infinity. You can set it to the desired number if you do not want to send, infinity data packets
- The size field specifies the data bytes to be sent and the delay specifies the time interval in milliseconds.
Click on send button
You should be able to see the following results
The title bar will show you the number of packets sent
Click on halt button to stop the program from sending data packets.
You can monitor the task manager of the target computer to see the network activities.
Summary
- A denial of service attack's intent is to deny legitimate users access to a resource such as a network, server etc.
- There are two types of attacks, denial of service and distributed denial of service.
- A denial of service attack can be carried out using SYN Flooding, Ping of Death, Teardrop, Smurf or buffer overflow
- Security patches for operating systems, router configuration, firewalls and intrusion detection systems can be used to protect against denial of service attacks.
More information
Posted by Ki-te at 6:17 PM 0 comments
BurpSuite Introduction & Installation
What is BurpSuite?
Burp Suite is a Java based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Because of its popularity and breadth as well as depth of features, we have created this useful page as a collection of Burp Suite knowledge and information.
In its simplest form, Burp Suite can be classified as an Interception Proxy. While browsing their target application, a penetration tester can configure their internet browser to route traffic through the Burp Suite proxy server. Burp Suite then acts as a (sort of) Man In The Middle by capturing and analyzing each request to and from the target web application so that they can be analyzed.
Everyone has their favorite security tools, but when it comes to mobile and web applications I've always found myself looking BurpSuite . It always seems to have everything I need and for folks just getting started with web application testing it can be a challenge putting all of the pieces together. I'm just going to go through the installation to paint a good picture of how to get it up quickly.
BurpSuite is freely available with everything you need to get started and when you're ready to cut the leash, the professional version has some handy tools that can make the whole process a little bit easier. I'll also go through how to install FoxyProxy which makes it much easier to change your proxy setup, but we'll get into that a little later.
Requirements and assumptions:
Mozilla Firefox 3.1 or Later Knowledge of Firefox Add-ons and installation The Java Runtime Environment installed
Download BurpSuite from http://portswigger.net/burp/download.htmland make a note of where you save it.
on for Firefox from https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/
If this is your first time running the JAR file, it may take a minute or two to load, so be patient and wait.
Video for setup and installation.
You need to install compatible version of java , So that you can run BurpSuite.
Read more
- Hacker News
- Pentest Usb
- Pentest Xss
- Hacking Ethics
- Pentest Tools Github
- Pentest +
- Hacker News
- Hacking Ethics
- Hacker Tools
- How To Pentest A Network
- Pentest +
- Hacking Health
- Hacker Lab
- Hacking Link
- Hacking Quotes
- Pentest Owasp Top 10
- Hacking Simulator
- Hacker0Ne
- How To Pentest A Website
- Pentest Devices
Posted by Ki-te at 1:31 PM 0 comments
Entropy: Netwave And GoAhead IP Webcams Exploiting Tool
About Entropy Toolkit
Entropy Toolkit is:
- A set of tools to exploit Netwave and GoAhead IP Webcams.
- A powerful toolkit for webcams penetration testing.
Entropy Toolkit's installationEntropy Toolkit's execution
Entropy Toolkit's examples:
- Example of exploiting a single webcam
entropy -b 1 -i [webcam's ip address and port] -v
Example:entropy -b 1 -i 192.168.1.100:80 -v - Example of exploiting webcams from a list
entropy -b 2 -l [file text] -v
Example:entropy -b 2 -l iplist.txt -v - Example of exploiting webcams using shodan
entropy -b 2 -v --shodan [you shodan api key]
Example:entropy -b 2 -v --shodan PSKINdQe1GyxGgecYz2191H2JoS9qvgD
Entropy Toolkit disclaimer:
Usage of the Entropy Toolkit for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state, federal, and international laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
Entropy Toolkit license: MIT license.
(Sign up Windscribe for free, get full protection and stay anonymous
with the best free VPN. Read more here)
Read more
Posted by Ki-te at 8:04 AM 0 comments
Wednesday, June 10, 2020
Hacking PayPal's Express Checkout
In this post we will tackle the following problems:
- How can PayPal's API be tested?
- How does PayPal's Express Checkout work? You can find the detailed report here.
- How can we debit more money than authorized?
How PayPal's API can be tested?
PayPal's Sandbox API
PayPal offers a feature called PayPal Sandbox Accounts, which mimics the production API. The basic idea is that a normal user/shop can test the API and make transactions without actually transferring money. This is the perfect tool for developers to test their API integration.Access to all messages
The next question is how to get access to all messages. All browser-related messages can be inspected, intercepted, and modified via BurpSuite. The main problem here is how to get access to the server-to-server exchanged messages: the messages exchanged between PayPal and a shop. In order to solve this problem, we deployed our own shop. For this purpose we used Magento, which already has a PayPal integration.Once we have our own controlled shop, we can enforce Magento to send all request through a proxy.
In the following picture you can see our setup.
 |
| Test suite for analyzing PayPal's API [1] |
In order to capture the traffic between our Magento hhop and PayPal we proceeded as follows:
- We configured Magento to use a proxy running on localhost:8081.
- We connected the proxy port on the virtual machine with our local machine via SSH remote port forwarding by issuing the following command
- We configured BurpSuite running on our local machine to listen on Port 8081 for incoming requests.
Please note that we uses our own, custom Magento shop in order to be able to test Paypal's API.
PayPal's Express Checkout
An overview of the checkout procedure is depicted in the following: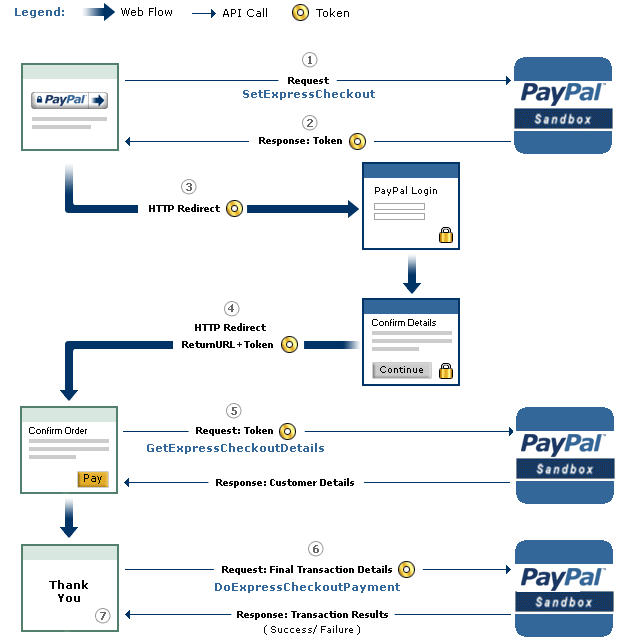 | ||||
| PayPal's Express Checkout [2] |
Step 1: Magento tells the PayPal API where to redirect the user after authorizing the transaction via the parameter RETURNURL and requests a token for this transaction.
Step 2: The PayPal API provides Magento with the token.
Step 3: Magento redirects the user to PayPal's website. The redirect contains the token from the previous step.
Step 4: The user authorizes the transaction. As a result, he will be redirected back to Magento (RETURNURL) with the token.
Step 5: Magento issues a request to the PayPal API to get the transaction details.
Step 6: Magento signals the PayPal API to execute the transaction.
Step 7: Magento serves the success page.
A more detailed view of the protocol and all parameters is shown on page 16 in the full version. We will concentrate only on step 6 and the parameters relevant for the attack.
The Attack
The goal of the attack is to let a shop (in our case Magento) debit more money than authorized by the PayPal user. The core of the attack is Step 6 -- DoExpressCheckoutPayment. Let's get a deeper look at this message: |
| Magento can raise the authorized amount and debit more money from the user's account |
- The shop sends the token, which was issued in the first step of the protocol and identifies uniquely the transaction through all steps.
- The PayerID referring to the user that authorized the payment.
- The AMT defining the amount, which will be transferred.
- The API Credentials authenticating Magento on PayPal.
- The Version pointing to the release number of the API.
As one can imagine, the core problem we found was the change of the AMT parameter. This value can be freely chosen by the shop, despite the fact that the user has authorized a different amount.
We tested only the SandBox API, but refused to test the production API in order to avoid problems. We promptly contacted PayPal's security team and described the problem hoping that PayPal can and will test the production API against the attack.
The response of PayPal can be summarized as follows:
- We don't get any BugBounty since we only tested the Sanbox API. (Fair enough)
- In the Production API PayPal this flexibility is a wanted feature. Thus, PayPal allows a merchant to charge for shipping and/or other expenses different amounts. Any malicious behavior can be detected by PayPal. In case of fraudulent charges the consumer are protected by the Buyer Protection policy.
Authors of this Post
Daniel HirschbergerVladislav Mladenov
Christian Mainka (@CheariX)
[1] BurpSuite Logo
[2] PayPal Express Checkout
More information
Posted by Ki-te at 7:28 PM 0 comments
HiddenWasp Linux Malware Backdoor Samples
Here are Hidden Wasp Linux backdoor samples.
Enjoy

Intezer HiddenWasp Malware Stings Targeted Linux Systems
8914fd1cfade5059e626be90f18972ec963bbed75101c7fbf4a88a6da2bc671b
8f1c51c4963c0bad6cf04444feb411d7
shell
f321685342fa373c33eb9479176a086a1c56c90a1826a0aef3450809ffc01e5d
52137157fdf019145d7f524d1da884d7
elf
f38ab11c28e944536e00ca14954df5f4d08c1222811fef49baded5009bbbc9a2
ba02a964d08c2afe41963bf897d385e7
shell
e9e2e84ed423bfc8e82eb434cede5c9568ab44e7af410a85e5d5eb24b1e622e3
cbcda5c0dba07faced5f4641aab1e2cd
elf shared-lib
d66bbbccd19587e67632585d0ac944e34e4d5fa2b9f3bb3f900f517c7bbf518b
2b13e6f7d9fafd2eca809bba4b5ea9a6
64bits elf shared-lib
2ea291aeb0905c31716fe5e39ff111724a3c461e3029830d2bfa77c1b3656fc0
568d1ebd8b6fb17744d3c70837e801b9
shell
8e3b92e49447a67ed32b3afadbc24c51975ff22acbd0cf8090b078c0a4a7b53d
33c3f807caea64293add29719596f156
shell
609bbf4ccc2cb0fcbe0d5891eea7d97a05a0b29431c468bf3badd83fc4414578
71d78c97eb0735ec6152a6ff6725b9b2
tar-bundle gzip contains-elf
d596acc70426a16760a2b2cc78ca2cc65c5a23bb79316627c0b2e16489bf86c0
6d1cd68384de9839357a8be27894182b
tar-bundle gzip
0fe1248ecab199bee383cef69f2de77d33b269ad1664127b366a4e745b1199c8
5b134e0a1a89a6c85f13e08e82ea35c3
64bits elf
More info
Posted by Ki-te at 1:10 AM 0 comments
Tuesday, June 9, 2020
How Block Chain Technology Can Help Fight Wuhan Corona Virus Outbreak
As the death toll and the infected cases of widespread coronavirus continue to increase, global organizations and the tech industry has come forward with technology like blockchain to fight coronavirus.
Along with the equipment and monetary support, technology also withstands against the virus with better plans and solutions. Hence, tech industries have started leveraging blockchain technology in the wake of a global health emergency.
Blockchain Helps In Real-Time Online Tracking
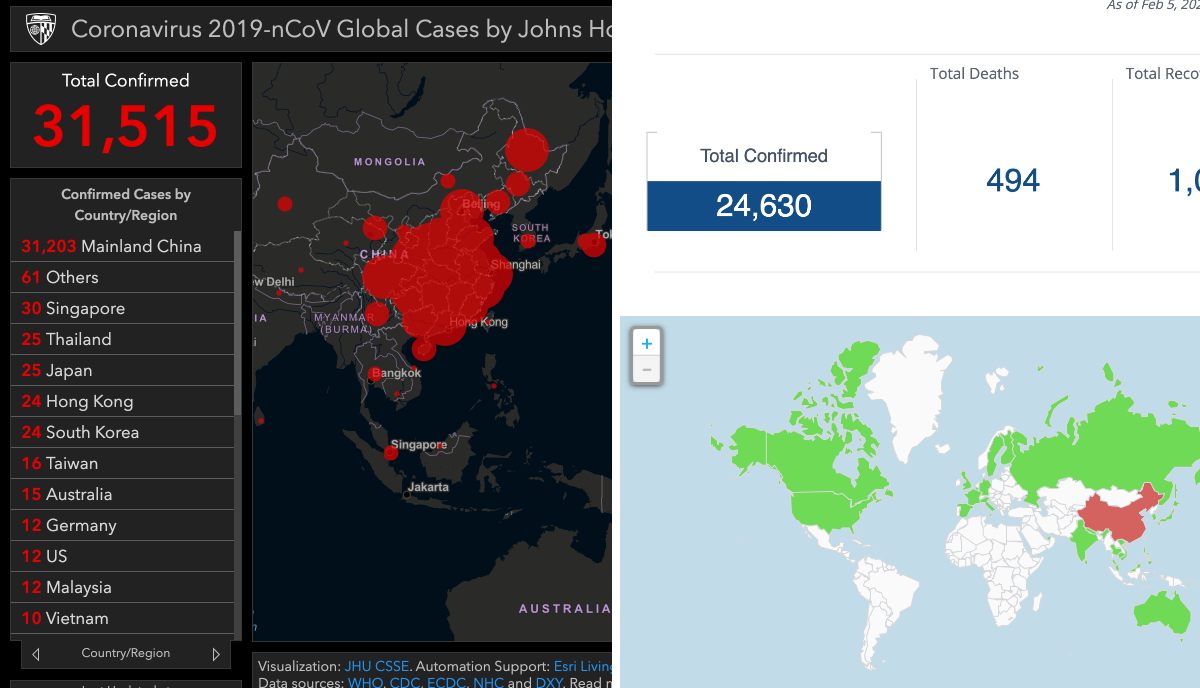
The Center for Systems Science and Engineering has already set up an online platform to track coronavirus and visualize the growing number of infected patients in real-time.
But Acoer, an Atlanta-based blockchain app developer, has also launched an alternative online data visualization tool to easily trail and depict the Cororanvirus outbreak using blockchain technology.
Acoer platform, named HashLog, is more advanced and clear as it pulls the data from the Hedera Hashgraph database using the HashLog data visualization engine.
Hedera Hashgraph is an immutable, transparent and decentralized database based on distributed ledger technology that provides synchronized and unchangeable data from the public networks.
Moreover, researchers, scientists, and journalists can use the HashLog dashboard to understand the spread of the virus and act against it swiftly.
For data sources, Johns Hopkins CSSE extracts data from WHO, CDC, ECDC, NHC, and DXY. On the other hand, Acoer maps the public data, including data from the Center for Disease Control (CDC) and the World Health Organization (WHO). Therefore, data may differ on both platforms.
Blockchain Can Help Monitor And Control Money Flow
To fight the further spread of the coronavirus (2019-nCoV) outbreak globally, China has also received abundant monetary support from the international community to create better action plans.
China's govt-led organization and charities are responsible for overseeing and utilizing the influx of money to research and generate a solution for coronavirus. But due to the lack of coordination and mismanagement among the various organization, money is not being laid out to curb the crisis.
Recently, a paper published by Syren Johnstone, from the University of Hong Kong, discusses the problems encountered by charities, in China and elsewhere. It argues that the present crisis should be seen as a call to arms.
Syren urges for a borderless solution with better management of donations and implementation using the emerging tech like Blockchain and Artificial Intelligence.
Keeping that in mind, Hyperchain, a Chinese company, also announced blockchain-based charity platform to streamline the donation from all over the world.
Since the Hyperchain platform is based on the blockchain, it offers more transparency among the sender and receiver of funds to bring trust and immutability to restrict the transaction data deletion.
Overall, Hyperchain improves administrative function for the money and also extends the logistics actions.
@HACKER NT
Continue reading
Posted by Ki-te at 3:00 PM 0 comments
TorghostNG: Make All Your Internet Traffic Anonymized With Tor Network
About TorghostNG
TorghostNG is a tool that make all your internet traffic anonymized with Tor network. TorghostNG is rewritten from TorGhost with Python 3.
TorghostNG was tested on:
- Kali Linux 2020a
- Manjaro
- ...
What's new in TorghostNG 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
Before you use TorghostNG
- For the goodness of Tor network, BitTorrent traffic will be blocked by iptables. Although you can bypass it with some tweaks with your torrent client 😥 It's difficult to completely block all torrent traffic.
- For security reason, TorghostNG is gonna disable IPv6 to prevent IPv6 leaks (it happened to me lmao).
Screenshots of Torghost (Version 1.0)
Connecting to Tor exitnode in a specific country:
torghostng -id COUNTRY IDChanging MAC address:
torghostng -m INTERFACEChecking IP address:
torghostng -cDisconnecting from Tor:
torghostng -xUninstalling TorghostNG:
python3 install.pyInstalling TorghostNG
TorghostNG installer currently supports:
- GNU/Linux distros that based on Arch Linux
- GNU/Linux distros that based on Debian/Ubuntu
- GNU/Linux distros that based on Fedora, CentOS, RHEL, openSUSE
- Solus OS
- Void Linux
- Anh the elder guy: Slackware
- (Too much package managers for one day :v)
To install TorghostNG, open your Terminal and enter these commands:
But with Slackware, you use
sudo python3 torghostng.py to run TorghostNG :vHelp
You can combine multiple choices at the same time, such as:
torghostng -s -m INTERFACE: Changing MAC address before connectingtorghostng -c -m INTERFACE: Checking IP address and changing MAC addresstorghostng -s -x: Connecting to Tor anh then stop :v- ...
I hope you will love it 😃
How to update TorghostNG
Open Terminal and type
sudo torghostng -u with sudo to update TorghostNG, but it will download new TorghostNG to /root, because you're running it as root. If you don't like that, you can type git pull -f and sudo python3 install.py.Notes before you use Tor
Tor can't help you completely anonymous, just almost:
- Tor's Biggest Threat – Correlation Attack
- Is Tor Broken? How the NSA Is Working to De-Anonymize You When Browsing the Deep Web
- Use Traffic Analysis to Defeat TOR
- ...
And please
- Don't spam or perform DoS attacks with Tor. It's not effective, you will only make Tor get hated and waste Tor's money.
- Don't torrent over Tor. If you want to keep anonymous while torrenting, use a no-logs VPN please.
Not anonymous: attack reveals BitTorrent users on Tor network
Changes log
Version 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
- Check your IPv6
- Change all "TOR" to "Tor"
- Block BitTorrent traffic
- Auto disable IPv6 before connecting to Tor
Contact to the coder
- Twitter: @SecureGF
- Github: @GitHackTools
- Website: GitHackTools 🙂
To-do lists:
- Block torrent, for you - Tor network (Done 😃)
- Connect to IPv6 relays (maybe?)
- GUI version
- Fix bug, improve TorghostNG (always)
And finally: You can help me by telling me if you find any bugs or issues. Thank you for using my tool 😊
Related articles
Posted by Ki-te at 10:17 AM 0 comments
Monday, June 8, 2020
Linux/AirDropBot Samples

MD5 | SHA256 | SHA1 |
|---|---|---|
85a8aad8d938c44c3f3f51089a60ec16 | 1a75642976449d37acd14b19f67ed7d69499c41aa6304e78c7b2d977e0910e37 | 2f0079bb42d5088f1fec341cb68f15cdd447ac43 |
2c0afe7b13cdd642336ccc7b3e952d8d | 64c0e594d4926a293a1f1771187db8cfb44a0dda80d8b25b4f0c975e1e77745c | fef65085a92654cbcf1e3e0d851c6cda8dd3b03d |
94b8337a2d217286775bcc36d9c862d2 | 71c02b99046c3be12e31577aa6623ce47dfb7f369e67af564d2bd499080c03b6 | d5deeb1b61026479acb421583b7b82d09d63e921 |
417151777eaaccfc62f778d33fd183ff | bf6941e644a430fef43afc749479859665a57b711d5483c2c7072049c7db17b7 | f76b9447db23229edae17a3160e04df41bc35a9d |
d31f047c125deb4c2f879d88b083b9d5 | 2785845c97a69e15c9c1535216732a9d24bcf8f7244ce7872a2b0d2d4bcb92c3 | 4693505ef4c029112c4b85a16762cf90f0d69c15 |
ff1eb225f31e5c29dde47c147f40627e | f7ab3d315961d84da43f30a186136a56f5aa1e9afe6b56a0d357accd5f0ab81a | d5f2a976b703b5e687ffc58c408e0bc880838ae7 |
f3aed39202b51afdd1354adc8362d6bf | fa2bc8d988c8dfbdc965f1373bd80e9f5862868397c1bcb5e84b1e9c1756e0e2 | 31f0bca917cfbffcc126219439d38fe80d5c8460 |
083a5f463cb84f7ae8868cb2eb6a22eb | d654850f7785a5adb34f0808e2952f66e3784c0a32427fab9e97c75f0a48d9f5 | ed4359a2805ce69771253d2257598b5c63c36c8e |
9ce4decd27c303a44ab2e187625934f3 | a2a245f12ae44cca79f03a465e2dc3dfa222dfcfda1017824b16abf397f16255 | 710e85ae3d362d3c8f3759319c308ff9b4dcdc86 |
b6c6c1b2e89de81db8633144f4cb4b7d | 2480be0d00193250bc9eb50b35403399ed44f53d5d919600ee5bab14ef769530 | ee77141054ac8d2fad062bcd79832b5f481c7dfb |
abd5008522f69cca92f8eefeb5f160e2 | 509299df2f6150f59ed777873d3b7c708587c68a4004b4654a8cf2a640dd50aa | 15cf94828c07e080b9c455738f3219859d9ab732 |
a84bbf660ace4f0159f3d13e058235e9 | 565deb4b1a7397d2497c75c9635b81d2e3b6427f0c576e5cd3c4224660712b56 | c56fea8c1c949394e539d5ab3e3df7dfd329844a |
5fec65455bd8c842d672171d475460b6 | 121c7ebfb99d8ef39f72bf7c787be4c15e2e08b731f01172605a4d34d27f08eb | 3b6ca4525c3aad0583400b911b015071a0ea6133 |
4d3cab2d0c51081e509ad25fbd7ff596 | 7f71577b63b449c1a9e9aa516fa9e4320fe5f79548a00025a430894a269ab57b | d521f25362791de4d8a82a2683f032c1dd816e74 |
252e2dfdf04290e7e9fc3c4d61bb3529 | 834fc5c0ccfde1f3d52d88355717f119221118ee2d26018b417c50d066e9e978 | c8f3130e64a6f825b1e97060cf258e9086a2b650 |
5dcdace449052a596bce05328bd23a3b | 22949a7a3424f3b3bdf7d92c5e7a7a0de4eb6bbe9c523d57469944f6a8b1d012 | f2c072560559a3f112e2000c8e28ee975b2b9db3 |
9c66fbe776a97a8613bfa983c7dca149 | 18c08d3c39170652d4770b2f7785e402b58c1f6c51ba1338be4330498ef268f4 | 18a99ec770109357d1adbc1c2475b17d4dcca651 |
59af44a74873ac034bd24ca1c3275af5 | 1c345b5e7c7fdcc79daa5829e0f93f6ae2646f493ae0ec5e8d66ab84a12a2426 | 98f789e91809203fbf1b7255bd0579fc86a982ba |
9642b8aff1fda24baa6abe0aa8c8b173 | 98165c65d83fd95379e2e7878ac690c492ac54143d7b12beec525a9d048bedae | bd447e0e77a9192b29da032db8e1216b7b97f9ed |
e56cec6001f2f6efc0ad7c2fb840aceb | 7a2bf405c5d75e4294c980a26d32e80e108908241751de4c556298826f0960f1 | b1c271d11797baac2504916ac80fd9e6fac61973 |
54d93673f9539f1914008cfe8fd2bbdd | c396a1214956eb35c89b62abc68f7d9e1e5bd0e487f330ed692dd49afed37d5a | 72a9b8d499cce2de352644a8ffeb63fd0edd414b |
6d202084d4f25a0aa2225589dab536e7 | c691fecb7f0d121b5a9b8b807c5767ad17ae3dd9981c47f114d253615d0ef171 | a68149c19bfddcdfc537811a3a78cd48c7c74740 |
cfbf1bd882ae7b87d4b04122d2ab42cb | 892986403d33acb57fca1f61fc87d088b721bdd4b8de3cd99942e1735188125b | a067a0cf99650345a32a65f5bc14ab0da97789b6 |
Posted by Ki-te at 8:35 PM 0 comments